You had a SOCKS5 proxy running perfectly on your local workstation. You migrated the same configuration to a cloud VM—an EC2 instance, a DigitalOcean droplet, whatever—and suddenly things broke. Maybe the proxy connection itself was refused. Maybe the proxy connected fine but the target account you were accessing flagged a suspicious login and demanded MFA. Or maybe it just timed out silently.
This is one of the more frustrating problems in proxy operations because the symptoms look random. The same credentials, the same proxy endpoint, the same target service—different outcomes depending on where you run the connection from. The confusion comes from not realizing that the phrase "SOCKS5 proxy login" actually spans two completely separate authentication events, and an environment switch can break either one independently.
This guide walks through the technical reasons cloud-to-local switching causes SOCKS5 login failures and warnings, how to identify which layer is broken, and how to fix each one. All guidance here is focused on legitimate use cases: security testing, enterprise network access, performance monitoring, and compliance verification.
The Two-Layer Authentication Problem
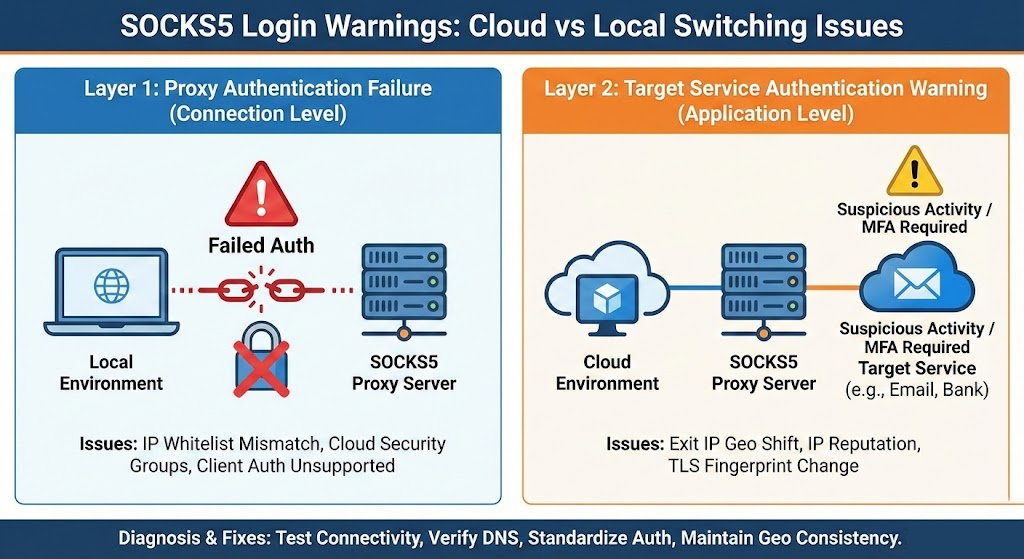
When you connect through a SOCKS5 proxy to reach a target service, two distinct authentication events happen in sequence. Understanding this separation is the key to diagnosing cloud/local switching failures.
Layer 1: Proxy Authentication — This is where your client authenticates to the proxy server itself. The SOCKS5 protocol, defined in RFC 1928, supports multiple authentication methods during the initial handshake. The client sends a list of supported methods, and the server picks one. For most commercial proxy services, this is either IP whitelisting (method 0x00, no authentication required because your source IP is pre-approved) or username/password authentication (method 0x02, defined in RFC 1929). With username/password auth, the server returns a STATUS byte: 0x00 for success, anything else for failure—and per the RFC, the server must close the connection on failure.
Layer 2: Target Service Authentication — After proxy authentication succeeds and your traffic is flowing through the proxy, you then log into the actual destination service (an email provider, a cloud platform, a banking portal). This login happens entirely at the application level. The target service sees the proxy's exit IP, evaluates it against its own risk models, and decides whether to allow access, challenge with MFA, or lock the account.
These two layers fail in completely different ways, and the symptoms are distinct:
Layer 1 failure produces connection-level errors: connection refused, authentication failed, HTTP 407 responses, or timeouts before you ever reach the target service.
Layer 2 failure lets you connect through the proxy just fine but triggers warnings on the target side: suspicious activity alerts, mandatory MFA challenges, "new device" notifications, or outright account lockouts.
When you switch from local to cloud (or vice versa), either layer can break. The trick is figuring out which one.
Why Cloud/Local Switches Break Layer 1
Several factors can cause proxy authentication itself to fail when you move between environments.
Egress IP changes invalidate IP whitelists. Many proxy providers offer IP-based authentication as an alternative to username/password. You whitelist your source IP, and the proxy server allows any connection from that address without credentials. The problem is obvious: your local workstation and your cloud VM have different public IP addresses. If you set up IP whitelisting on your local machine and then run the same config from a cloud instance, the proxy sees an unrecognized source IP and rejects the connection outright. Cloud IPs are also frequently dynamic—especially on platforms where instances stop and start with new addresses. Keeping whitelists current across cloud deployments is an ongoing maintenance burden.
Cloud security groups block outbound proxy ports. On AWS, the default EC2 security group allows all outbound traffic. But in hardened or production environments, security teams often restrict egress rules to specific ports and destinations. SOCKS5 proxies commonly listen on port 1080, though many providers use non-standard ports. If your cloud instance's security group doesn't have an outbound rule allowing TCP traffic to the proxy server's IP and port, the connection will be refused or time out. According to AWS VPC documentation, if a security group has no outbound rules, no outbound traffic is allowed. This is the same config that worked on your laptop where no such restrictions existed—a frustrating inconsistency if you don't know to check.
Client software differs in SOCKS5 auth support. This is a particularly common trap. Chromium-based browsers (Chrome, Edge, Brave) do not support SOCKS5 username/password authentication natively. This has been an open issue in the Chromium bug tracker for over a decade. Firefox supports it, and command-line tools like curl handle it well with --proxy-user or URL-embedded credentials. So here's the scenario: you test your SOCKS5 proxy with curl on your local machine—works fine. You set up a cloud VM with a GUI, open Chrome, configure the SOCKS5 proxy—authentication fails. You didn't change the proxy. You changed the client, and the new client doesn't support the auth method you're relying on. Workarounds include running a local forwarding proxy (tools like gost can chain a no-auth local SOCKS5 listener to an authenticated upstream) or using browser extensions like FoxyProxy that handle SOCKS5 auth at the extension level.
DNS resolution mode mismatches. SOCKS5 has a subtle but important distinction: socks5:// resolves DNS locally before proxying, while socks5h:// sends the hostname to the proxy for remote resolution. If your local machine resolves a hostname to one IP but the cloud VM (with a different DNS resolver) resolves it differently, you get inconsistent behavior. In curl, the difference is explicit:
# Local DNS resolution (DNS may leak to your ISP/cloud resolver) curl -x socks5://proxy.example.com:1080 https://target.com # Remote DNS resolution through the proxy curl -x socks5h://proxy.example.com:1080 https://target.com
On your local workstation, local DNS resolution might work fine because your ISP resolves correctly. On a cloud VM, the cloud provider's internal DNS resolver might return different results or fail for certain domains entirely.
Why Cloud/Local Switches Break Layer 2
Even when the proxy connection itself is solid, the target service can still reject you based on risk signals that change between environments.
Exit IP geolocation shifts. When you access a service from your local machine through a proxy, the target sees the proxy's exit IP. When you move to a cloud VM, you might use a different proxy endpoint or pool, resulting in a different exit IP in a different geographic location. Target services—especially email providers and financial platforms—actively track the geographic pattern of your logins. A sudden jump from, say, a US-based residential IP to a German datacenter IP within minutes triggers location-based anomaly detection.
IP reputation and ASN classification. Cloud provider IP ranges (AWS, GCP, Azure) are well-known and often flagged in commercial IP intelligence databases. Services like Google and Microsoft maintain lists of IP ranges associated with cloud infrastructure and apply stricter scrutiny to logins from those addresses. A residential proxy exit IP from a local connection might pass reputation checks cleanly, while the same account accessed from a cloud-hosted proxy endpoint using datacenter IPs hits an immediate risk flag.
TLS and browser fingerprint changes. Switching environments often means switching the entire software stack. Your local machine runs a particular OS, browser version, and TLS library that produce a specific TLS fingerprint (including the JA3/JA4 hash). A cloud VM running a different OS, headless browser, or Python script produces a completely different fingerprint. Sophisticated target services compare the TLS fingerprint against historical patterns for your account and flag mismatches.
Diagnosing Which Layer Failed
Before you start fixing things, you need to identify which layer is causing problems. Here's a practical diagnostic approach.
Step 1: Test proxy connectivity independently. Use curl to verify that you can authenticate and connect through the proxy from your cloud environment, without involving any target service login:
# Test basic SOCKS5 connectivity and auth # Replace with your actual proxy credentials and endpoint curl -x socks5h://username:password@proxy.example.com:1080 \ https://api.ipify.org?format=json \ --connect-timeout 10 -v
If this command returns a JSON response showing an IP address, Layer 1 is working. If it fails with a connection error, timeout, or authentication failure, the problem is at Layer 1.
Step 2: Check the error type. The error message tells you a lot:
Connection refused— The proxy server's port is unreachable. Check security groups, firewall rules, and confirm the proxy endpoint is correct.SOCKS5 authentication failedorHTTP 407— Your credentials are wrong or your source IP isn't whitelisted. Verify credentials and check if the provider requires IP whitelisting from the new cloud IP.Connection timed out— Traffic isn't reaching the proxy at all. This is almost always a firewall or security group issue on the cloud side.You connect and browse fine, but the target service shows a security warning — Layer 1 is fine. The issue is Layer 2 risk detection on the target service.
Step 3: Verify DNS behavior. Check whether DNS resolution is happening where you expect:
# Compare local resolution vs proxy resolution # This resolves DNS locally curl -x socks5://proxy:port https://target.com -v 2>&1 | grep "resolv" # This resolves DNS through the proxy curl -x socks5h://proxy:port https://target.com -v 2>&1 | grep "resolv"
If you see your cloud VM resolving hostnames locally when you expected proxy-side resolution, switch to the socks5h:// scheme.
Fixing Layer 1 Issues
For IP whitelist problems: Update your proxy provider's whitelist to include your cloud instance's public IP. If your cloud IP is dynamic, consider switching to username/password authentication instead, or assign an Elastic IP (on AWS) or a Reserved IP (on DigitalOcean) to stabilize the address.
For security group issues: Add an outbound rule allowing TCP traffic to your proxy server's IP and port. On AWS:
aws ec2 authorize-security-group-egress \
--group-id sg-YOURGROUP \
--ip-permissions 'IpProtocol=tcp,FromPort=1080,ToPort=1080,IpRanges=[{CidrIp=PROXY_IP/32}]'Adjust the port number to match your proxy provider's actual listening port.
For client auth compatibility: If you're using a Chromium-based browser on the cloud VM, set up a local forwarding proxy to handle authentication. Using gost (a Go-based tunnel tool):
# Install gost, then run a local no-auth SOCKS5 listener # that forwards to your authenticated upstream proxy gost -L socks5://:11080 -F socks5://username:password@proxy.example.com:1080
Then point your browser at 127.0.0.1:11080—no authentication required at the local level because gost handles it upstream.
Fixing Layer 2 Issues
Layer 2 problems are fundamentally about risk signals. You can't "fix" the target service's security policies, but you can reduce the signals that trigger them.
Keep exit IP geography consistent. If your workflow involves logging into accounts that are associated with a specific region, ensure your proxy exit IP matches that region. Suddenly switching from a US residential IP to an EU datacenter IP will almost certainly trigger alerts. Residential proxies are particularly valuable here because their IPs originate from real ISPs, carrying higher trust scores in commercial IP intelligence databases than cloud or datacenter IPs.
Avoid rapid geographic jumps. If you need to switch regions, introduce a reasonable time gap. Services track the physical plausibility of location changes—logging in from New York and then Tokyo within 30 minutes is an obvious red flag.
Use consistent client environments. When possible, standardize your browser version, OS, and TLS configuration between local and cloud setups. This reduces fingerprint-based anomaly detection. If you're running automation, ensure the headless browser on your cloud VM produces a TLS fingerprint consistent with what the account has seen historically.
Compliance and Safety Notes
SOCKS5 proxies are legitimate network tools used for security testing, compliance verification, enterprise access management, and authorized data collection. However, it's important to note that accessing third-party services through proxies must comply with those services' terms of use. The diagnostic and troubleshooting steps in this article are intended for authorized access to accounts you own or have permission to manage.
If you're conducting security assessments or ad verification audits, document your methodology and ensure you have appropriate authorization. Proxy use for circumventing platform security controls on accounts you don't own is outside the scope of this guide.
Keeping Your SOCKS5 Setup Stable Across Environments
A few preventive practices make cloud/local switching less painful over time.
Use username/password authentication instead of IP whitelisting when your source IPs are dynamic. It's slightly less convenient but dramatically more portable. Always test proxy connectivity independently before debugging application-level issues—a 30-second curl test can save an hour of chasing the wrong layer. Standardize your DNS resolution mode across environments by always using socks5h:// for remote resolution, eliminating DNS inconsistency as a variable. And keep a record of your proxy provider's port requirements and authentication methods so you can configure security groups and client tools correctly on the first attempt when spinning up new cloud infrastructure.
Environment switches will always carry some risk of disruption. But when you understand that SOCKS5 login issues span two independent authentication layers—and you know the specific triggers that break each one—diagnosis becomes systematic rather than a guessing game.
Looking for residential SOCKS5 proxies that stay reliable across environments? Proxy001 provides residential proxy IPs with full SOCKS5 support, username/password authentication that works consistently whether you're connecting from a local machine or a cloud VM. With IPs sourced from real ISPs across 190+ locations, you get the geographic targeting and IP reputation needed to avoid Layer 2 risk flags—without the instability of free or shared proxy pools. Proxy001's infrastructure is built for teams that need predictable proxy behavior in production, not just in testing. Explore plans and start a trial →